Study shows bias of left and right extends to perceptions of verifiable fact. Politics has seeped into every corner of our lives. Even announcements once thought above rank partisanship, such as states letting voters mail their ballots this fall and the death toll from the COVID-19 pandemic, now ignite accusations of political bias.. This work analyzes the decentralized identification data registry and compares the performance of verifiable data registry based on blockchain and the Distributed Hash Table (DHT) on different scales of systems and shows that DHT has better performance. User identification in decentralized systems is a demanding task. Identification systems should work resiliently and have efficient performance.

Digital Forensics and Cyber Crime Datamining

Proposed blockchainbased verifiable user data access control policy. Download Scientific Diagram
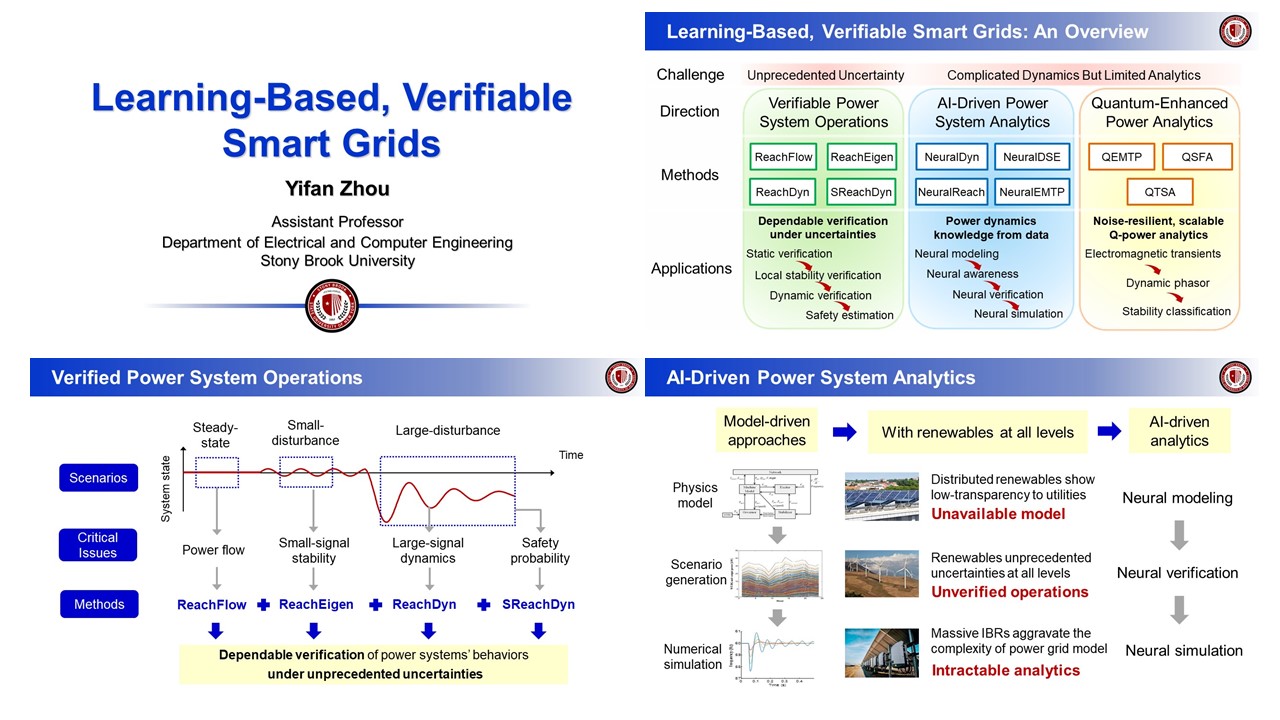
LearningBased, Verifiable Smart Grids Yifan Zhou

Simulation Model Verification and Validation in the Modelling Process Download Scientific Diagram

(DOC) Data Analysis and Verification of Qualitative Research Psychology Lover Academia.edu
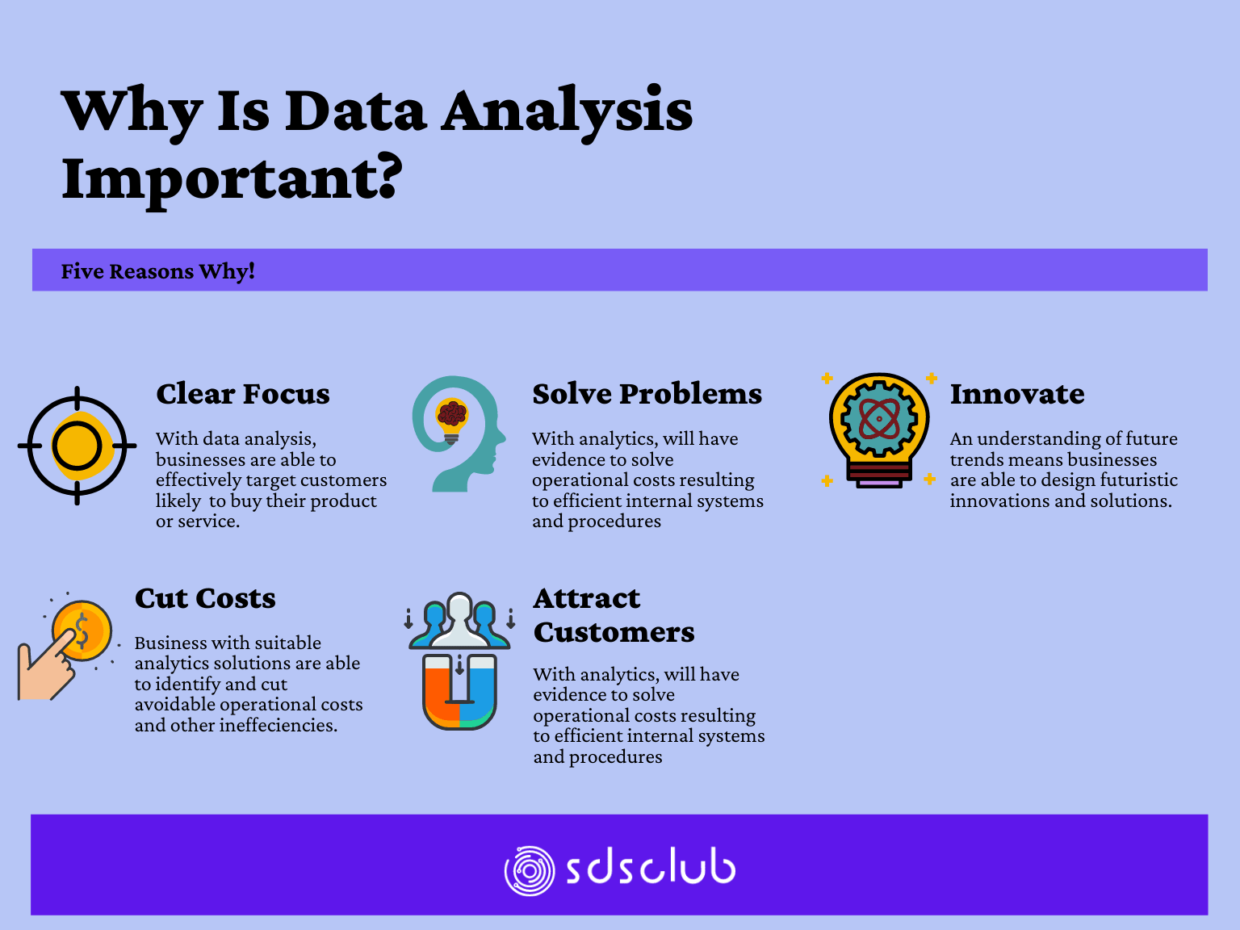
5 Data Analysis Techniques That Can Surprise You SDS Club
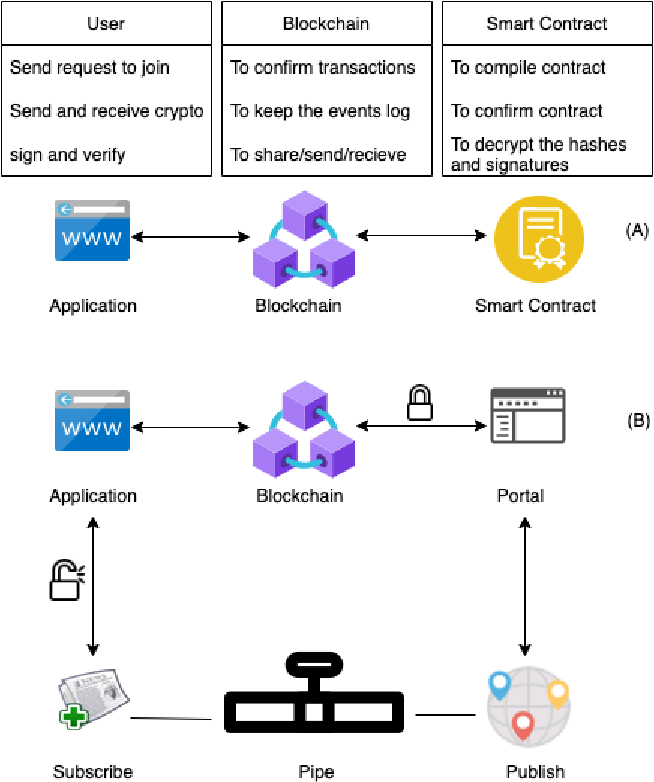
Figure 1 from Performance Analysis of Verifiable Data Registry Solutions for Decentralized

Security analysis of a publicly verifiable data possession scheme for remote storage Request PDF

Publicly verifiable data transfer and deletion scheme for cloud storage Changsong Yang

Data collection, query, and source data verification process using… Download Scientific Diagram

Data Management Process Flow Diagram
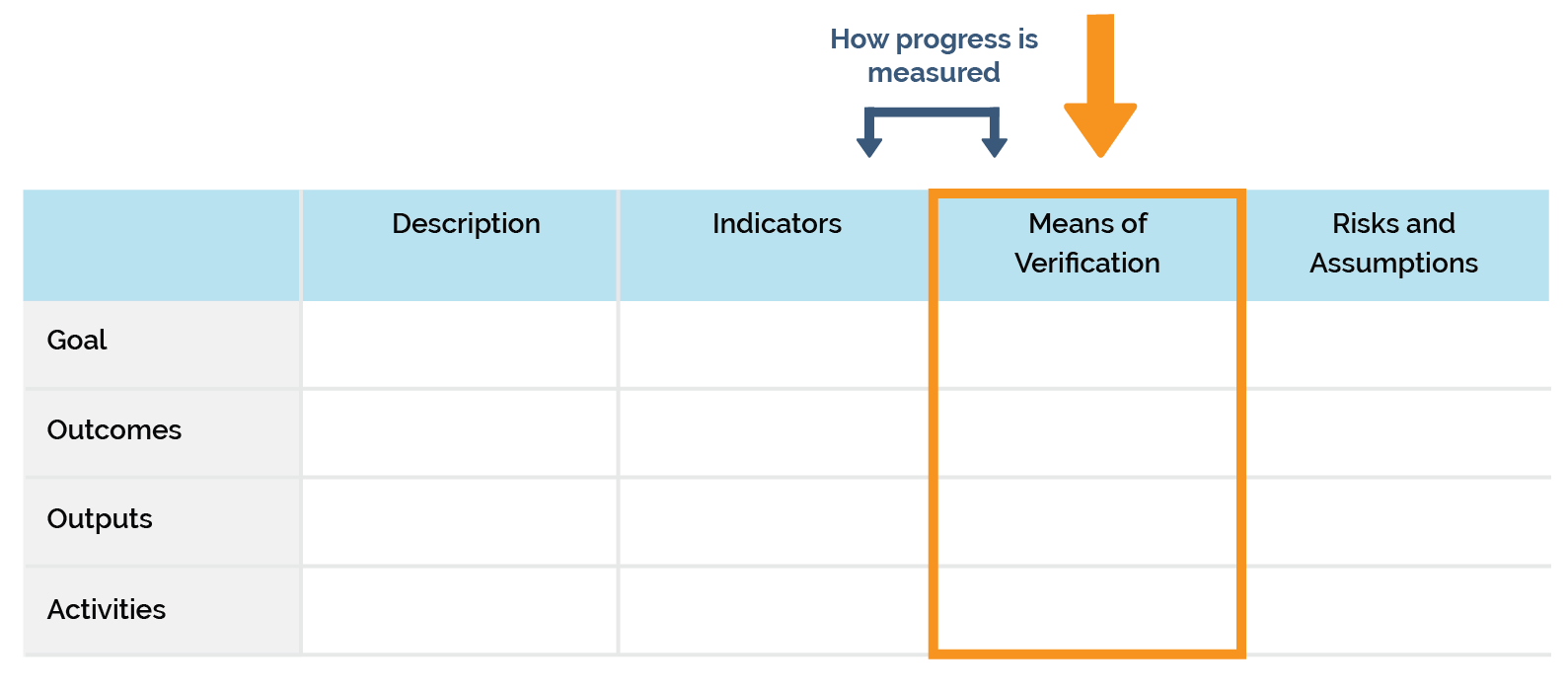
Means of Verification/Data Collection CVE Reference Guide for

(PPT) Chapter 1 Descriptive Analysis. Statistics Making sense out of data. Gives verifiable

(PDF) Data Flow Analysis as a General Concept for the Transport of Verifiable Program Annotations

Data Collection and Verification Steps Download Scientific Diagram
Application model verification and validation methods Download Scientific Diagram
Data Validation Techniques YouTube

Visual Verification And Validation Model Infographic.tv Number one infographics & data

Free Profitability Analysis The Real Authority
Top 15 Data Analysis Tools For Managing Data Like A Pro
The basic data model of W3C verifiable credentials may be familiar to developers and architects that are used to working with attribute-based credentials and data technologies. The issuer, or the authority on some information about a subject (e.g. a person), issues a credential containing this information in the form of claims to a holder.. The proof can be also based on the analysis of the adversary’s advantage in the security experiment Exp A CPA-M-II. The original input, verifiable data and the shares received by the computing nodes are shown in Fig. 5. As can be seen, in the view of the computing nodes, both the input and verifiable data are meaningless images, making it.